In recent years, ransomware has become one of the biggest cybersecurity threats to businesses and organizations. Recently, major Vietnamese companies including VNDirect and PVOIL have been targeted by ransomware attacks that deliberately disrupted operations and caused economic damage. Therefore, solutions for cybersecurity and information security are becoming a major concern for organizations and businesses in the context of increasingly sophisticated and cunning threats from the internet environment.
What is ransomware?
Ransomware is a type of malicious software designed to encrypt user data or lock access to data on a computer system. To regain access to the data, hackers demand that victims pay a ransom, often in cryptocurrencies like Bitcoin. Ransomware typically spreads through phishing email attachments, malicious websites, or through unpatched security vulnerabilities in software.
Ransomware is also known as extortion software or ransom malware.
WannaCry is a well-known example of ransomware that spread globally in 2017. The WannaCry attacks originated in the UK and spread to nearly 150 countries, primarily targeting government agencies and large businesses. According to Interpol, the WannaCry malware attacked about 230,000 computers across 150 countries.

Ransomware - Immage source: Foxbusiness
The most "headache" type of ransomware
Among the types of ransomware, encrypting ransomware is the most common and also the most dangerous. Once it infiltrates the victim's computer system, it establishes a secret connection to the hacker's server and encrypts all user data with a private key that can only be decrypted using a key stored on the attacker’s server. The user's data files are then changed to specific formats like *.docm or *.cerber, and error messages appear when the victim tries to access them. In many cases, decrypting and recovering the data is nearly impossible when hackers use cryptographic hash functions of 128-bit or higher.
Recently, some cybercrime groups have even developed "Ransomware-as-a-Service" (RaaS) business models, allowing non-professional attackers to purchase encrypting ransomware services. This has increased the dissemination of this "difficult-to-treat" type of malware.
How to prevent ransomware
For users
Proactively back up data
Proactively backing up important data is always an effective measure against ransomware. Once you have your data back-up, you no longer have a reason to pay a ransom to hackers, right? Data can be backed up to secure cloud platforms such as Google Drive, OneDrive, iCloud. These platforms all allow free data backup with enough capacity for regular users
Stay away from phishing emails
In this daily job, the more emails you send to the internet environment, the greater your risk of receiving phishing emails. Signs of phishing emails include:
- Sent from a domain name that looks reputable but is actually a fake domain name, the content is written in general terms, not related to your work
- Sent from a generic address eg: info@acb.com, contact@xyz.com
- Send to a series of people, the identifier "unclosed-receipent"
- The email does not identify the sender and has no contact phone number
- Emails with attached documents are compressed files, you don't know what's inside
- Due to being distributed in large numbers, phishing emails are often automatically identified as "SPAM" by the system.
Be careful with email attachments
Attachments sent via email have always been a popular method of distributing malware for criminals in cyberspace. Normally, you should question attachments with the following signs:
- The attachment was sent from an unfamiliar email or from an untrusted domain
- Attachment compressed with winrar or winzip sent from a strange email with unrelated content
- Absolutely do not click on attachments with the extension *.exe (Windows operating system) and *.dmg (iOS operating system)
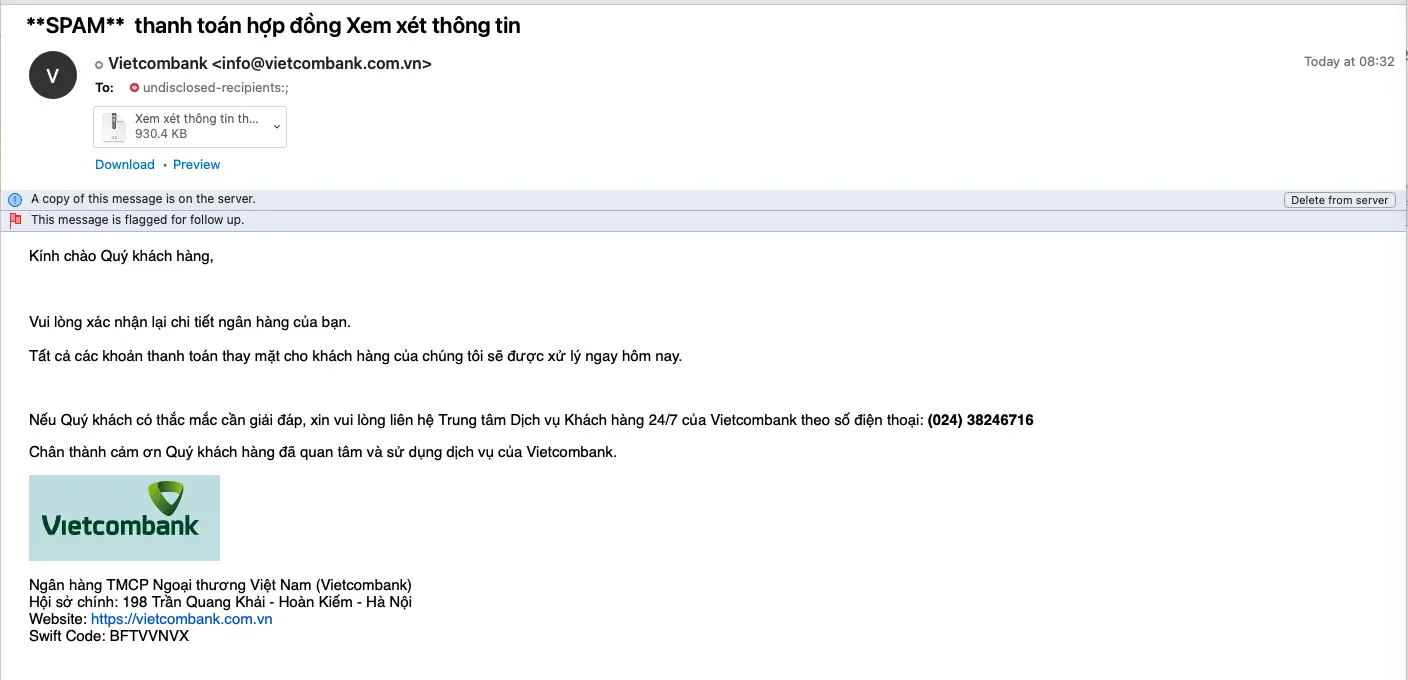
An example of phishing email
For Businesses
Be proactive in prevention work
Businesses and organizations are recommended to be more proactive in preventing cyber attacks. Large businesses and organizations need to build a team of IT engineers specialized in network safety and security to protect the system and be ready to handle unsafe incidents that may occur to ensure losses in lowest level.
Invest in hardware and software systems
Currently on the market there are many hardware and software products that support system security and prevent network attacks developed and provided by reputable brands such as Cisco, Fortinet, Palo Alto, Juniper... Most of these products use cryptography to secure data or create VPN (virtual private network) tunnels to secure data exchanged over the internet. To ensure that products are imported and traded in accordance with state regulations, businesses should look to buy from suppliers who have licenses to sell civil cryptographic products. In the case of purchasing directly imported goods from manufacturers, businesses may also need a reputable consulting company, or an importer of record service provider to be able to import products at a reasonable cost.
Vulnerability review and network security testing
Besides building a team dedicated to your business's network information security, you may still need testing services from professional providers. Network information security testing services include:
- Monitor network information security, analyze transmission data
- Penetration testing
- Consulting on building solutions for network information security
Please leave a comment and share the article if you find it useful in your work
↓ ↓ ↓ ↓ ↓ ↓ ↓